Every crypto trilemma - 10 unsolved triangles in blockchain and web3
Here are 10 triangles to tease your brain. A list of every trilemma I have come across related to blockchain, web3 and finance.
Crypto loves trilemmas. I compiled every trilemma I have come across that is related to blockchain, web3 and finance. Through examining these trilemmas, we could uncover the unique problems that the industry is facing. Perhaps by studying these tricky triangles and addressing the difficult design choices, the next killer application or use case will eventually emerge.
List of trilemmas below, links to the source are provided if you want to dig deeper:
Scalability Trilemma
Stablecoin Trilemma
Alternative Stablecoin Trilemma
DeSoc Trilemma
On-chain credit Trilemma
Blockchain Privacy Trillema
Interoperability Trilemma
Bridging Trilemma
GameFi Trilemma
CBDC Trilemma
(And 2 Bonus Trilemmas, Find out below!)
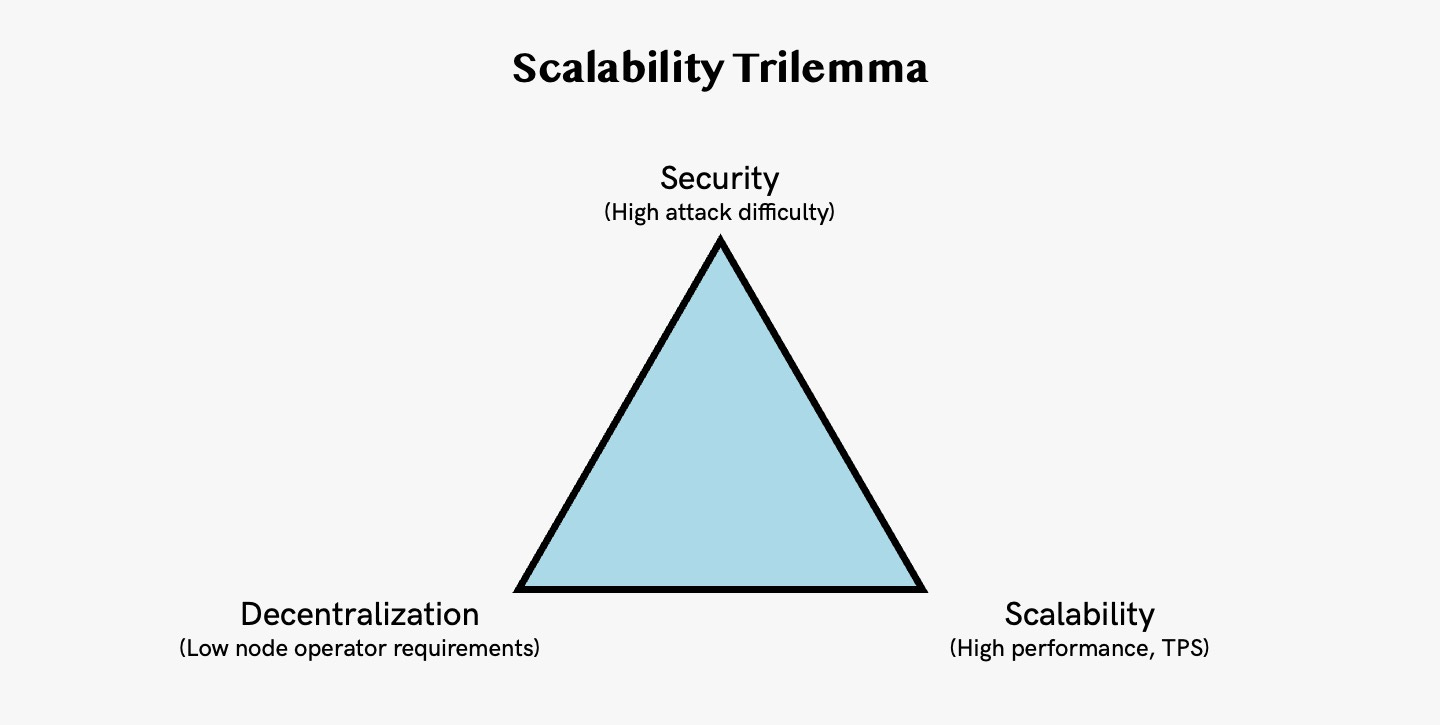
1. Blockchain Scalability Trilemma
Blockchain scalability trilemma refers to the proposition that public blockchains must sacrifice either security, decentralization, or scalability.
Decentralization → Applying decentralized processes eliminates the role of intermediaries. Decentralized networks crowdsource consensus, meaning that no one entity can control or censor the data that transacts through it. However, achieving optimal decentralization tends to decrease network throughput.
Security → To increase network throughput on a blockchain network, there's an incentive to reduce the distribution of blockchain nodes either geographically or in number. This results in greater centralization and reduces security on blockchain networks. When consensus is achieved on an open network with limited nodal distribution, a 51% attack is more probable as hackers can amass the required hashing power with ease.
Scalability → Scalability refers to the blockchain’s ability to support high transactional throughput. This means that as use cases and adoption accelerate, the performance of the blockchain would not suffer. In other words, it refers to how much a network can grow in the future while maintaining the same speed and output.
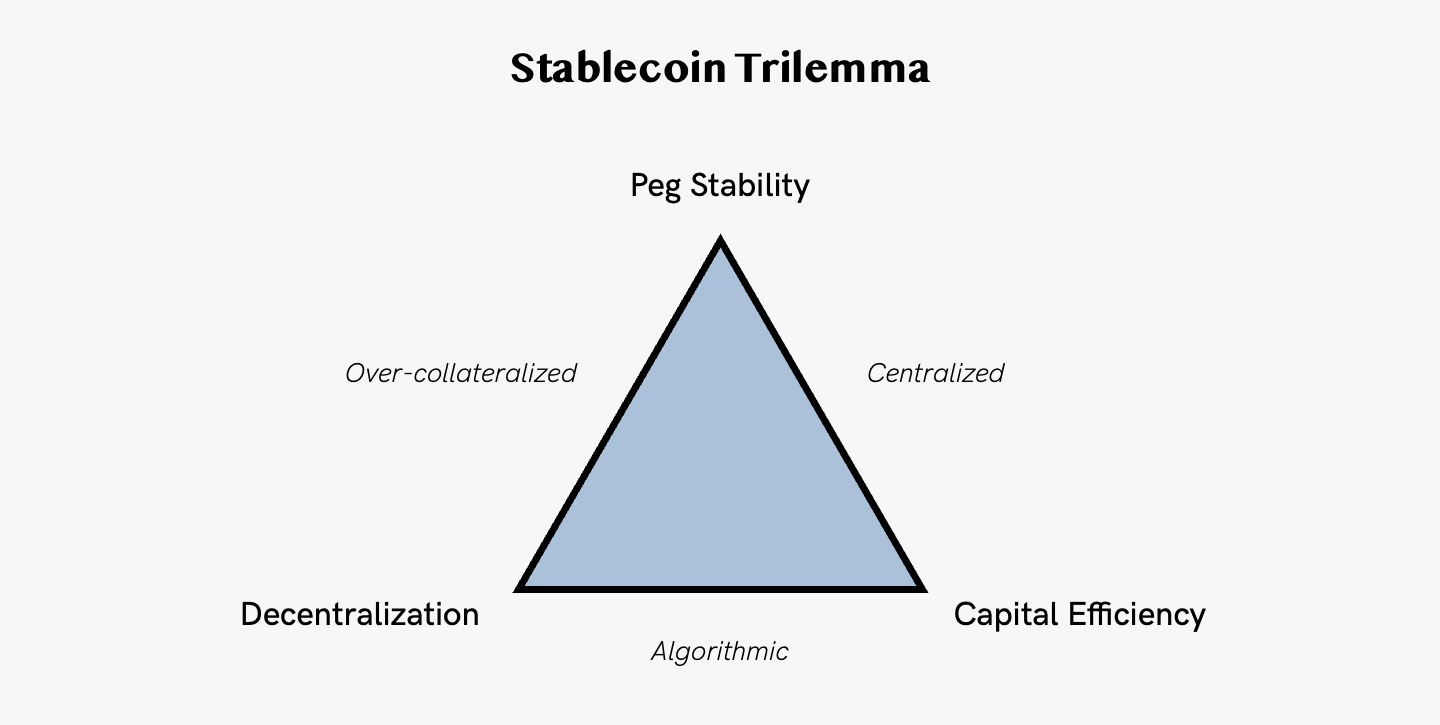
2. Stablecoin Trilemma
The three main objectives of a stablecoin design are: capital efficiency, decentralization and peg stability.
Peg Stability → Price stability in par with the pegged assets is the main objective of any stablecoin. This is usually achieved through a collateralization of the issued stablecoin based on the underlying asset. In the case of an US-pegged stablecoin, a 1:1 USD collateralization could ensure that every stablecoin outstanding is always backed with one USD.
Capital Efficiency → The capital efficiency describes how much value is needed to create one unit of the issued stablecoin. A high capital efficiency is needed in order to scale a stablecoin. If for instance, more capital than $1 is needed to create one USD-pegged stablecoin, the stablecoin design would be described capital-inefficient.
Decentralization → Stablecoins have become an integral part of DeFi and the wider web3 ecosystem. A decentralized stablecoin would not rely on the governance of an intermediary and avoid centralized single-points-of-failure and risks.
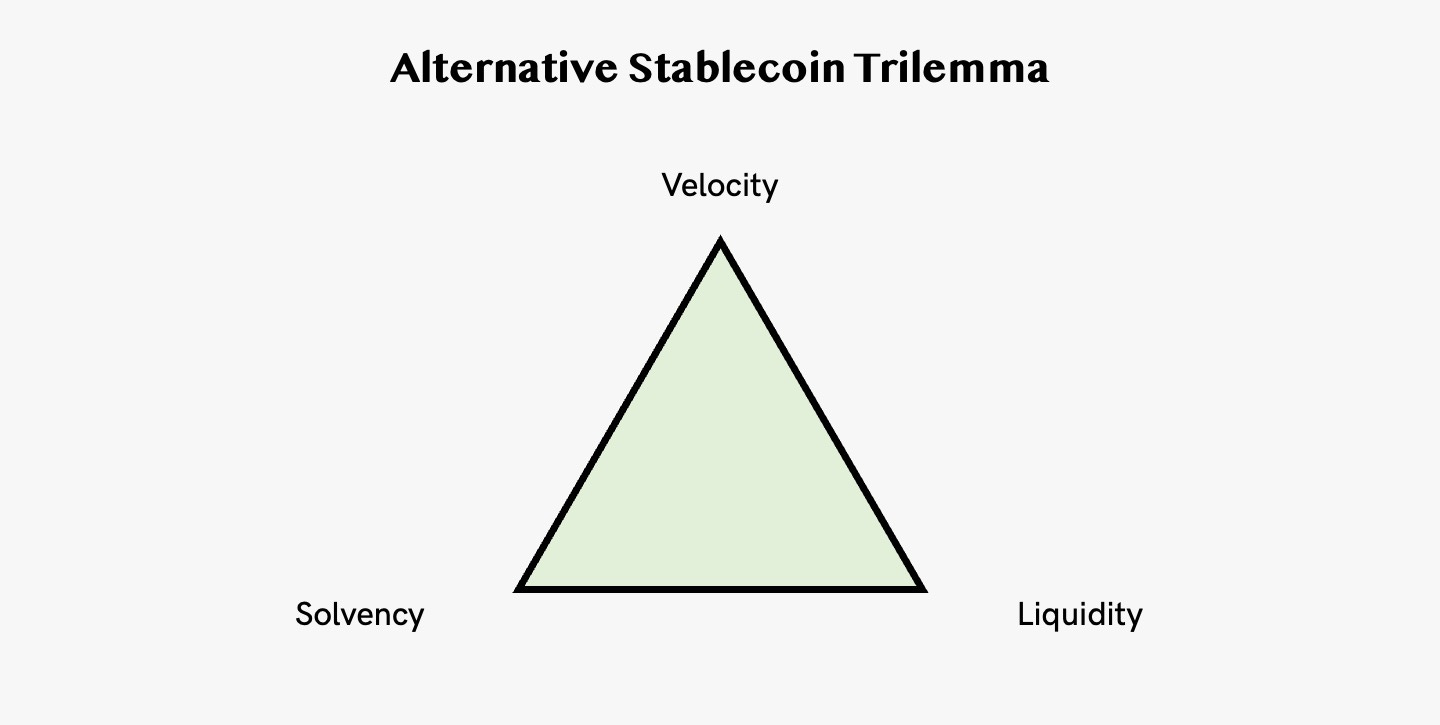
3. Stablecoin Trilemma (Alternative)
An alternative stablecoin trilemma is laid out by Luca Prosperi in his blog Dirt Roads. He discusses the trade-offs between Velocity, Liquidity and Solvency of a stablecoin design.
Velocity → How easy it is for a stablecoin to scale up (similar to the idea of capital efficiency). In order to promote ultra-fast scaling Terra opted for a reflexive system where the protocol could print new money without the need to inject exogenous collateral into the system — at the expense of liquidity and solvency, with the hope to rebalance the system at a later stage. MakerDAO went the opposite direction, leaving money printing and burning to market dynamics — or to organic demand for leverage.
Solvency → How reliable is the value backing the currency (similar to peg stability). The viability of a currency will always be linked to the quality of the assets backing it — and to its governance mechanisms. Maker’s over-collateralisation model offered solid assurances to $DAI holders and kept the protocol alive amid multiple market downturns.
Liquidity → How robust is the peg against short-term shocks. Even solvent stablecoin designs that sacrifice speed of deployment in exchange of extreme protectionism are continuously exposed to market forces. The relative value of an asset vs. another is a function of short-term supply and demand dynamics and in a pegged system there is little tolerance for volatility.
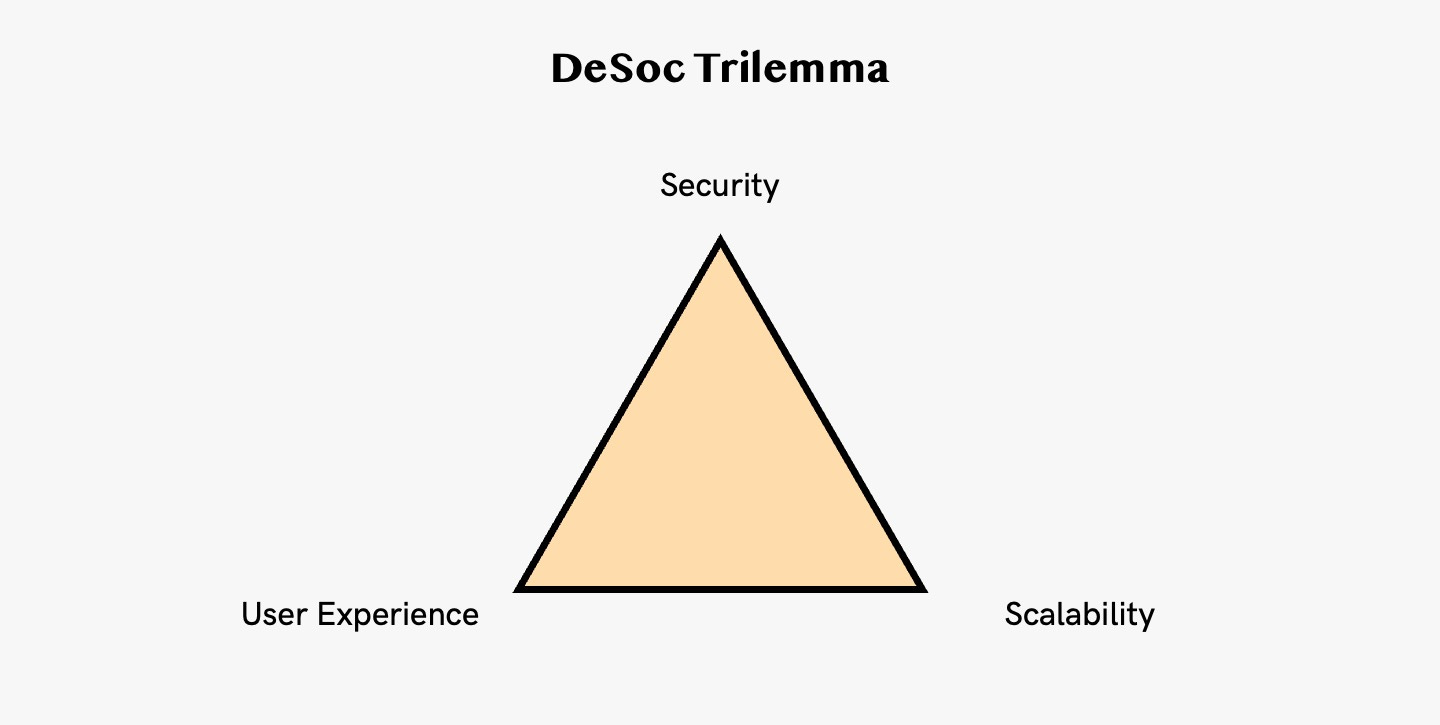
4. Decentralized Social Media Trilemma
Web3 expands the idea of social networks. One conception is a web3 social graph: it maps profiles, followers, and their connections. Users can then consume content and interact with their social graphs. DeSoc solves some of the problems in web2 social media but it introduces its own set of complications. DeSoc Trilemma highlights the tradeoffs made in security, scalability, and user experience (UX).
Security → Security indicates two things: decentralization of a blockchain as well as the executor of transactions. Decentralization of a blockchain: with more validators, blockchains become more decentralized and secure. However, this introduces the tradeoff between security and scalability. The more decentralized and secure a blockchain is, the harder it is to scale. That explains why no DeSoc protocol could truly live on Ethereum, as the gas fees are too high. For the time being until Zk-rollups become cheap and usable, a DeSoc protocol needs to operate either on a sidechain, sub/supernet, or a standalone L1.
User Experience → When it comes to the execution of transactions, some DeSoc protocols do that themselves. For example, a user follows someone and only signs a message to make this happen. They don’t pay the gas fee or actually execute the transaction, instead this role falls onto the protocol itself. This introduces the tradeoff between security and UX. Obfuscating gas fees is a massive step forward in UX. the ultimate UX is one where you connect your wallet but never have to deal with metamask pop ups prompting you to sign contracts or pay for transactions. This comes at the cost of giving further permissions and control of your wallet to smart contracts.
Scalability → The tradeoffs made between UX and scalability are trickier. Take for example, DeSo is a blockchain specifically created for social applications. It has scaled to over 1.5 million users but it lacks the surrounding ecosystem such as gaming and DeFi protocols. Value-additive composability benefit does not exist on DeSoc protocols built on stand alone blockchains.
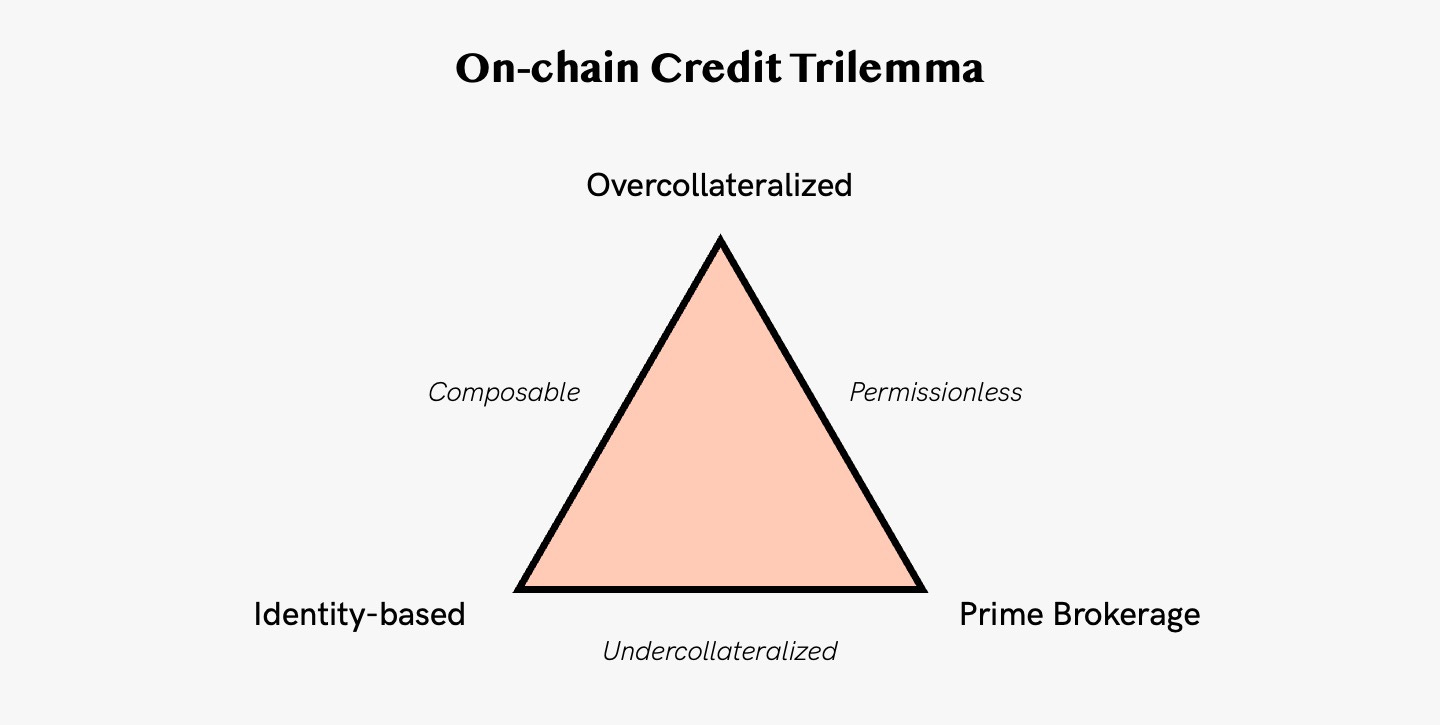
5. On-chain credit trilemma
Jump Crypto’s model explores the three major categories of on-chain credit: overcollateralized, prime brokerage, and identity-based.
Overcollateralized → Overcollateralization is the provision of collateral that is worth more than enough to cover potential losses in cases of default. Overcollaterized lending is currently the predominant model in DeFi. It epitomizes the benefits of the on-chain approach: anybody can lend to, borrow from, or build atop the protocol, with no requirements for identifying information or third-party gatekeepers. Protocols like Compound, AAVE and MakerDAO all requires overcollateralization.
Prime Brokerage → Rather than enforcing overcollateralization in an open system, simulate undercollateralization in a closed system by restricting the use of funds. By creating a large but well-defined boundary via an interface or set of integrations, a protocol can deliver the benefits of undercollateralized lending while remaining technically overcollateralized by retaining ultimate control of the assets. It is “borrowing in a bubble” as algorithmic security: you can’t default, because the code won’t let you.
Identity-based → Both the overcollateralized and prime brokerage approaches impose limitations on credit, restricting either the types of leverage obtainable (overcollateralized) or the available uses of capital (prime brokerage). In order to enable fully general-purpose loans, where borrowers truly can run off with the money, it requires imposing broader consequences for the borrower, which is sociolegal security: you won’t default, because you will be punished off-chain.
6. Blockchain Privacy Trilemma
This is another one inspired by Vitalik’s scalability trilemma. Obscuro, a privacy-focused Ethereum L2, proposes the privacy trilemma in the context of blockchain.
Privacy → Defined as the ability to keep transactions hidden from all participants, including any sequencers or miners.
Programmability → Ability to be Turing complete and solve for all use-cases.
Decentralization → The degree to which you can move beyond a single entity controlling a critical aspect of the solution, leaving no single point of failure. For example, centralized sequencers or aggregators.
Example approaches in this model include:
UTXO ZKP - Many blockchains exist that aim to optimize specifically for token transfers. Z-Cash is an example of one of these blockchains. It’s UTXO based with support for zero-knowledge proofs (ZKP) to allow for the transfer of tokens privately. You can’t, however, use it to build something like Uniswap or AAVE as it simply doesn’t support the notion of Autonomous Agents.
zkSync/STARK - Where decentralization, scalability, censorship resistance and all the other great promise of blockchain is not required, then ZKPs become an interesting option to provide privacy with the power of smart contracts. They can maintain privacy over this operation by creating a ZKP and passing it to a sequencer. But if the sequencer goes down, the whole network goes on hold, so it is against decentralization.
Ethereum - Ethereum is a global computer; every node that is part of the network runs the same smart contract code and needs to collectively agree on the ordering of events for contract accounts. In a UTXO system, only user accounts exist, and their ordering is inherent. This allows for only the user to create a proof and convince the network of its validity. To achieve the same privacy ZKPs provide UTXO systems on Ethereum, you would require every node to be part of the group that sees everything — no privacy.
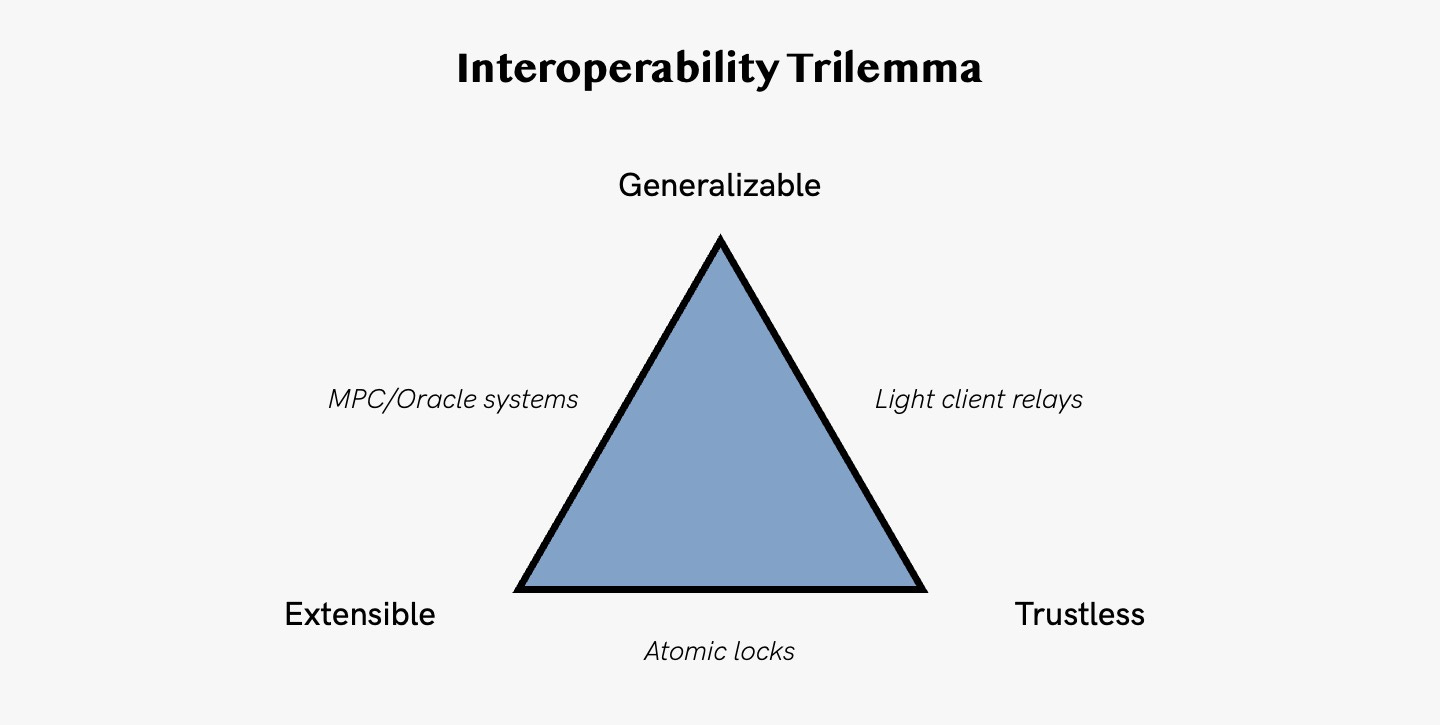
7. Interoperability Trilemma
The interoperability trilemma states that InterOp protocols can only have two of the following three properties:
Trustlessness → The protocol has equal security to the underlying blockchain. It does not add new trust assumptions.
Extensibility → The protocol’s ability to connect different blockchains.
Generalizability → The protocol can pass any piece of cross-chain data, from tokens to messages to contract calls.
Arjun Bhuptani classifies bridges into three buckets (natively verified, locally verified, externally verified) depending on which two trilemma properties are baked into a bridge’s design:
Natively verified bridges — Trustless and Generlizeable (Cosmos IBC, Near Rainbow Bridge)
Locally verified bridges — Trustless and Extensible (Connext, Hop)
Externally verified bridges — Extensible and Generalizable (Multichain, Hyphen)
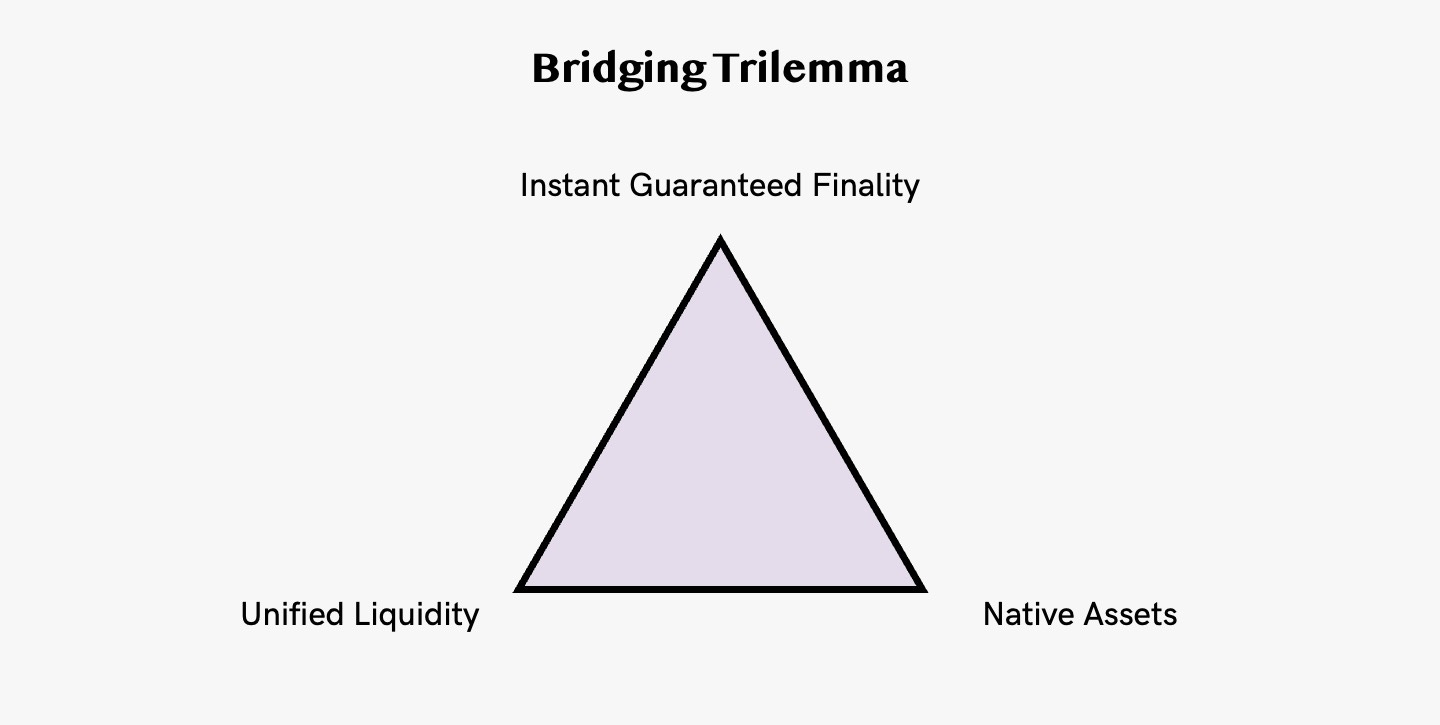
8. Bridging Trilemma
The bridging trilemma states that when designing bridges, builders must choose only one or two of the following features:
Instant Guaranteed Finality → Users and applications are guaranteed to receive funds on the destination chain immediately after a transaction has been executed on the source chain and the transaction reaches finality on the destination chain.
Unified Liquidity → A single liquidity pool is used between different chains rather than having separate pools for different tokens.
Native Assets → Users receive native assets on the destination chain after bridging instead of wrapped assets minted by the bridges themselves.
Examples of bridge designs falling short of the bridging trilemma:
Lock and mint bridges — Such bridges offer instant guaranteed finality. However, users receive a synthetic or wrapped asset on the destination chain, not the native asset. (Example: Wormhole, Multichain)
Liquidity networks with pools of native assets with unified liquidity — In such designs, there’s a single pool on one chain connected with additional pools on all the other chains with shared access to each other’s liquidity. As a result, these bridge designs cannot offer instant guaranteed finality since a transaction can fail due to a lack of liquidity in the shared pools. (Examples: Biconomy’s Hyphen, cBridge’s pool-based bridge)
9. GameFi Trilemma
Playability → Playability has two layers. The first layer is how smooth the game is running on the blockchain. If players are constantly facing the long network congestion, volatile gas fee and convoluted process of buying/selling game assets, then the game is not really playable. The second layer is how fun the game really is.
Accessibility → Accessibility refers to the barrier preventing people to participate play2earn games. Many GameFi projects require a prior investment to the games’ asset. Though the player can then make money from play2earn mechanics, the monetary aspect prevents non-crypto people from participating the game.
Profitability → The profitability is the financial return for the money, time, and energy the player invests in the game. The issue with profitability is, to make the game play-to-earn, the game must quantify the player’s in-game performance. For example, completing a set of daily tasks or winning a PvP battle must be result-orientated. However, game experience should come from both the game process and the result. Profitability determines how long the players will put up with the game’s grinding mechanics until they burn out.
10. CBDC Trilemma
A central bank digital currency, or CBDC, may provide an attractive alternative to
traditional demand deposits held in private banks. When offering CBDC accounts, the central bank needs to confront classic issues of banking: conducting maturity transformation while providing liquidity to private customers who suffer “spending” shocks. While the central bank can always deliver on its nominal obligations, runs can nonetheless occur, manifesting themselves either as excessive real asset liquidation or as a failure to maintain price stability.
In general, one would like a central bank to deliver three goals. First, we want financial stability – that is, to avoid the spending runs. Second, we want efficiency – that is, that the economy achieves the optimal risk-sharing between patient and impatient agents (or, equivalently, the optimal maturity transformation between short-run deposits and long-run investment projects). Third, we want price stability – that is, prices do not change too fast and disrupt allocations, for instance because most contracts are expressed in nominal terms.
Linda Schilling et al. demonstrate that the central bank can always implement the socially optimal allocation in dominant strategies and deter central bank runs at the price of threatening inflation off-equilibrium. If price-stability objectives for the central bank imply that the central bank would not follow through with that threat, then allocations either have to be suboptimal or prone to runs.
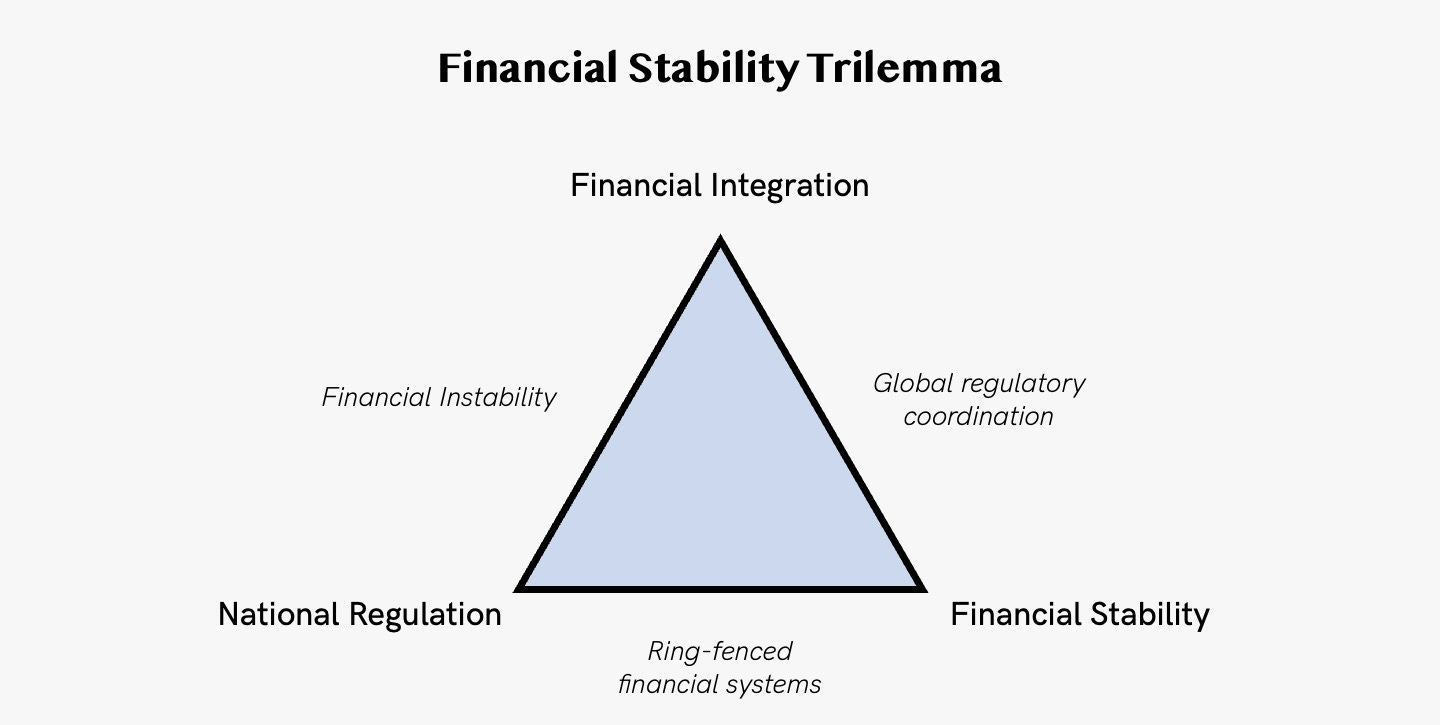
[Bonus 1] Financial Stability Trilemma
According to this trilemma (1) national financial policy, (2) cross-border financial integration, and (3) financial stability are incompatible. For example, if the objectives are financial integration across borders and a stable financial system, financial policy cannot be national.
In essence, when financial integration increases in a region, the incentives among national supervisors to act in a way that preserves financial stability in the region as a whole decreases. If the benefits of stability oriented policies spread to the region as a whole, the willingness of national supervisors to bear the cost of these polices decline.
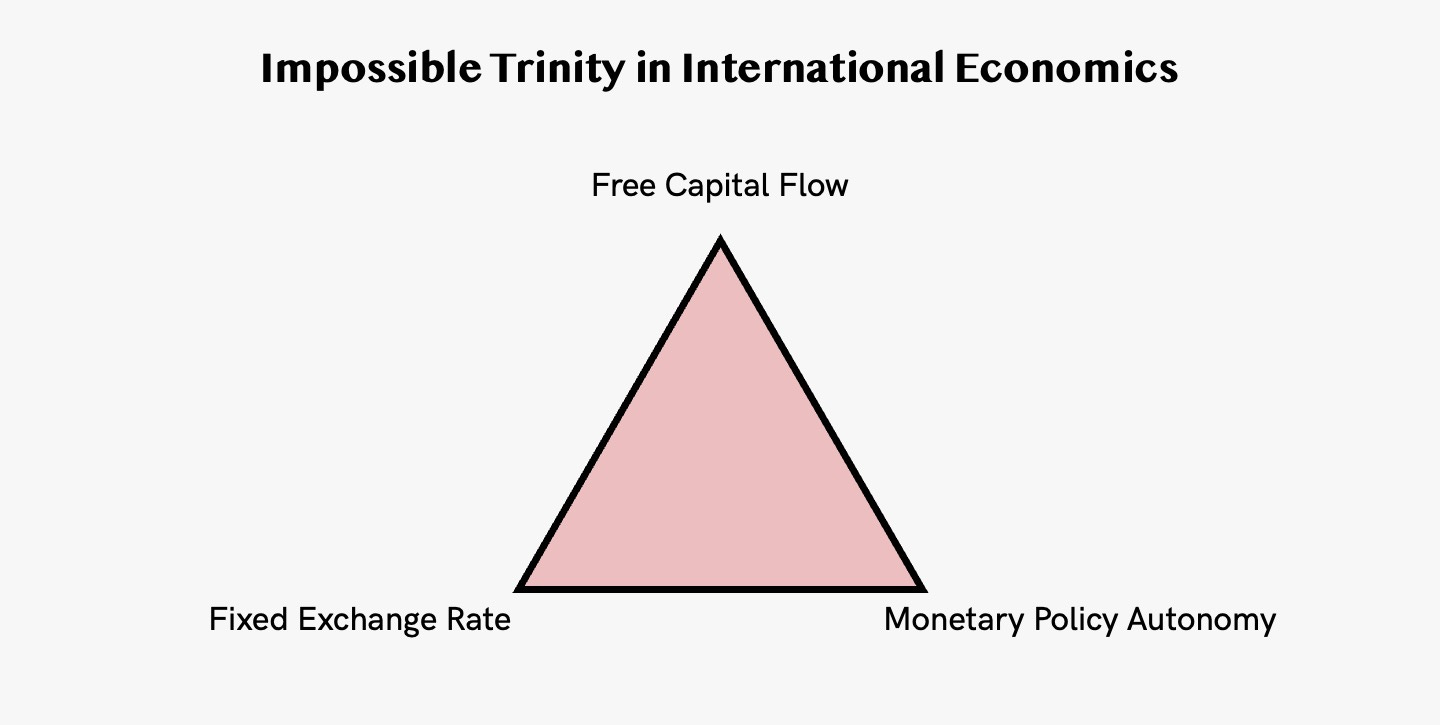
[Bonus 2] Impossible trinity in international economics
When making fundamental decisions about managing international monetary policy, the impossible trinity suggests that countries have three possible options from which to choose. According to the Mundell-Fleming trilemma model, these options include:
Setting a fixed currency exchange rate
Allowing capital to flow freely with no fixed currency exchange rate agreement
Autonomous monetary policy